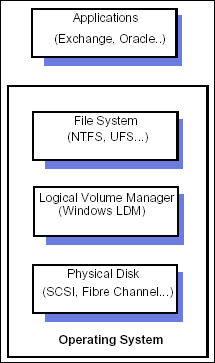
The storage management requirements of an enterprise computing environment can be rather complex. Modern operating systems take a layered approach to manage this complexity.

At the bottom layer is physical storage, which is typically some type of fixed, magnetic hard disk or disk array. Disk devices communicate with the host computer via standardized protocols such as SCSI or IDE. Sometimes a Storage Area Network protocol (such as Fibre Channel) provides an underlying transport layer for the SCSI protocol. Communication with physical disk devices is managed by software components of the operating system called device drivers.
Above the physical device drivers, Windows operating systems provide a Logical Volume Management layer. Logical Volume Management allows the system administrator to use physical disk storage in more efficient and flexible ways. For example, the LVM layer usually permits a physical disk to be divided into several logical partitions that may be formatted and used independently. Some LVMs can combine several physical disks into one virtual disk with additional performance or fault tolerance features (for example, the RAID configurations.) The LVM features built into the operating system may be replaced or enhanced by third-party LVM products. The LVM may write certain data structures, such as partition tables, to reserved areas on the physical disks. This information is called metadata. LVM virtual disks are presented to upper layers of the system as block-addressable storage devices, with the same characteristics as the underlying physical disks. The ideal LVM is essentially transparent to the layers above it.
The layer above the Logical Volume Manager is called the file system. The file system presents a higher-level logical view of the data. Typically the file system view consists of a hierarchy of nested folders or directories and individual files. The features and attributes of files may vary from one type of file system to another. For example, NTFS file systems track ownership and per-user access rights on each file, whereas FAT provides no file security whatsoever. In addition to the users' data, the file system stores its own data structures, or metadata, on the disk. The file system may incorporate read ahead or write-behind caching to improve performance. File system caching and other features are carefully designed to ensure the consistency of user data and metadata on the disk. Some file systems take special steps to preserve metadata consistency in the event of a system crash.
Above the file system, and outside the scope of the operating system in general, there is application software. Simple applications, such as word processors, use the standard file system interface provided by the operating system to store their data. More sophisticated applications like Database Management Systems (DBMS) and messaging services may use special file system features or even raw logical volumes. Each application maintains its own data structures. Service-based applications like DBMS often implement their own caching strategies and employ special measures to protect the consistency of the data and metadata.
The preceding discussion illustrates the way that each layer in the storage model introduces a new level of abstraction. At each level, the operating system or the application carefully preserves the consistency of user data and metadata. Any data protection or storage management system that interacts with the lower levels of the model must take steps to preserve the consistency of data and metadata associated with the layers above.