
  |
Follow the steps given below to install the Exchange Agents in clustered environment on the following:
Where to Install |
Related Topics |
The following procedure describes the steps involved
in installing the Exchange Agents for Exchange Server 2003 on the following:
|
Provides step-by-step procedure to download the latest packages for software install. Verify that the computer in which you wish to install the software satisfies the System Requirements. Provides comprehensive information on firewall. |
The below mentioned prerequisites are for Mailbox Agents only. Ensure that you have the following:
| 1. |
Log on to the computer using an account with the following privileges:
|
|||
| 2. | Run Setup.exe from the Software Installation Package. | |||
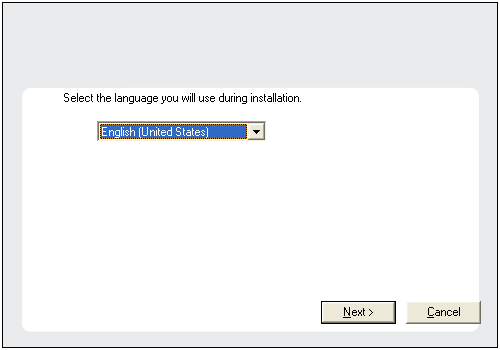
| 3. |
Select the required language. Click Next. |
 |
||
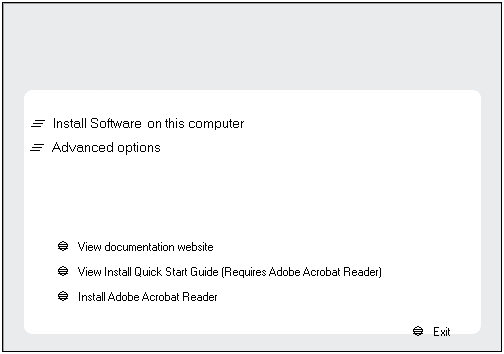
| 4. |
Select the option to install software on this computer.
|
 |
||
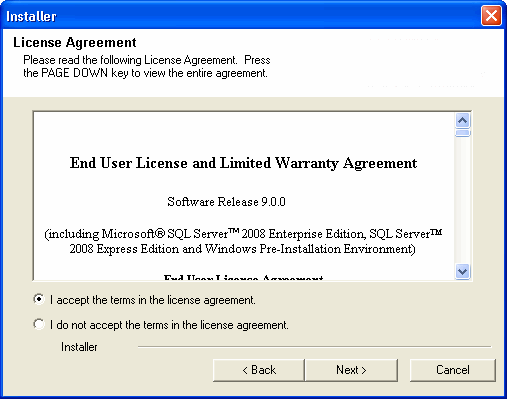
| 5. |
Select I accept the terms in the license agreement. Click Next. |
 |
||
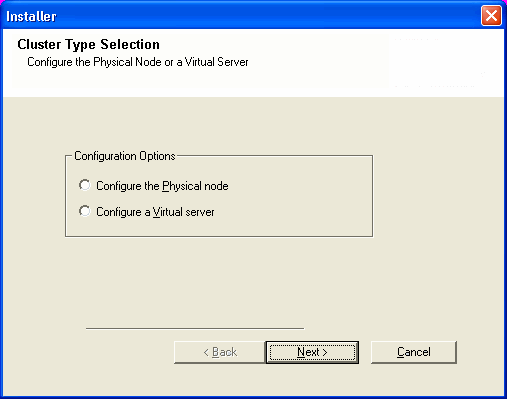
| 6. |
Select Configure a Virtual Server. Click Next. |
 |
||
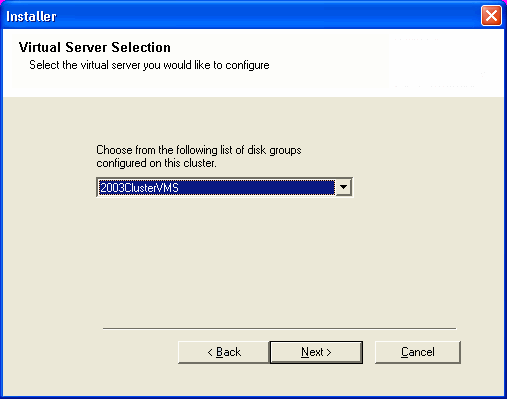
| 7. |
Select the disk group in which the virtual server resides. Click Next. |
 |
||
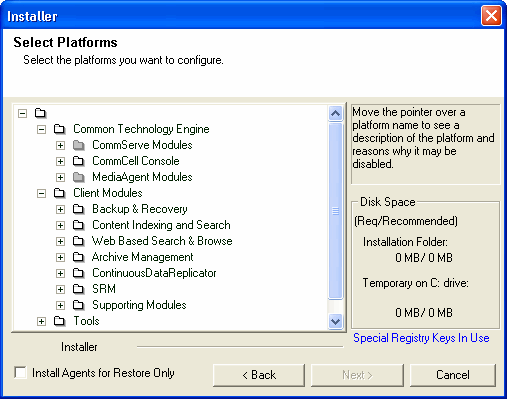
| 8. | To install the Exchange
iDataAgents expand Client Modules | Exchange, and select
one or more of the following:
To install the Exchange Archiver Agents, expand Client Modules | Archive Management, and select one or more of the following:
Click Next.
|
 |
||
| 9. |
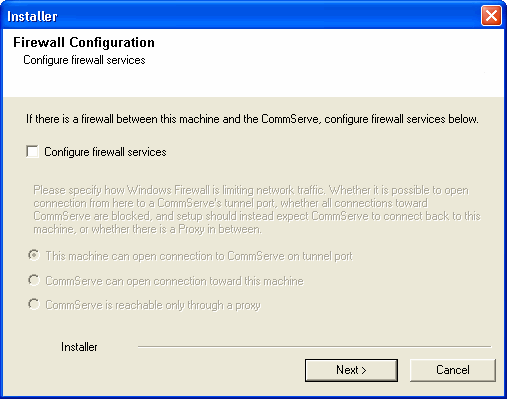
If this computer and the CommServe is separated by a firewall, select the Configure
firewall services option and then click Next.
For firewall options and configuration instructions, see Firewall Configuration and continue with the installation. If firewall configuration is not required, click Next. |
 |
||
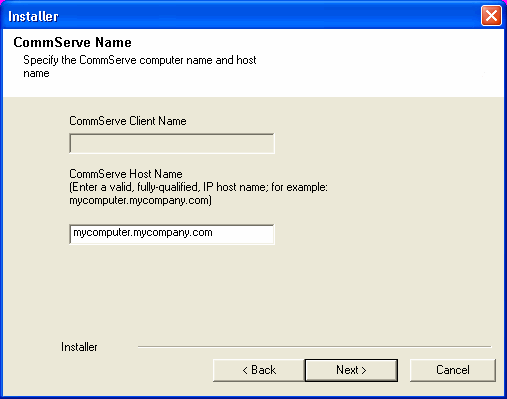
| 10. |
Enter the fully qualified domain name of the CommServe
Host Name. Click Next.
|
 |
||
| 11. | Click Next. |
 |
||
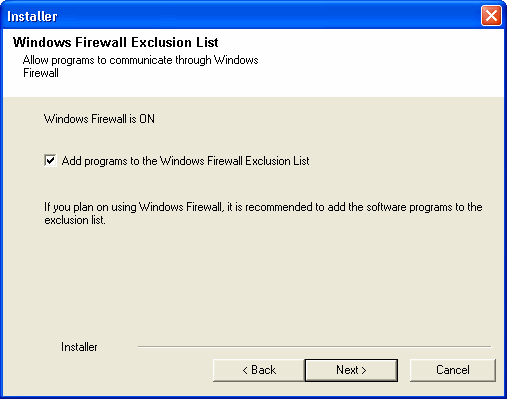
| 12. |
Select Add programs to the Windows Firewall Exclusion
List, to add CommCell programs and services to the Windows Firewall
Exclusion List. Click Next.
|
 |
||
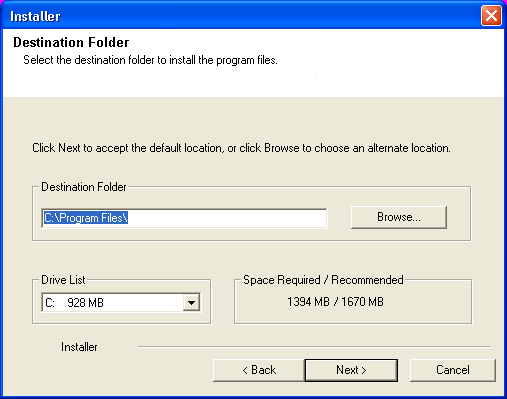
| 13. |
Verify the default location for software installation. Click Browse to change the default location. Click Next.
|
 |
||
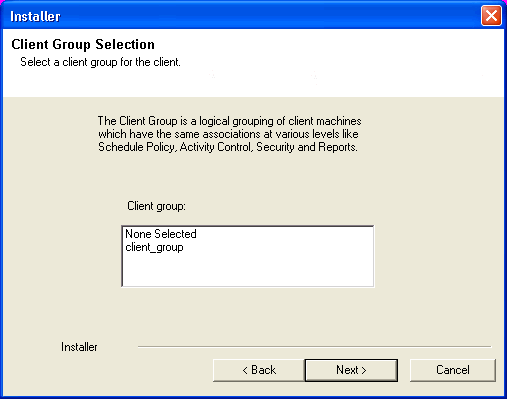
| 14. |
Select a Client Group from the list. Click Next.
|
 |
||
| 15. | Click Next. |
 |
||
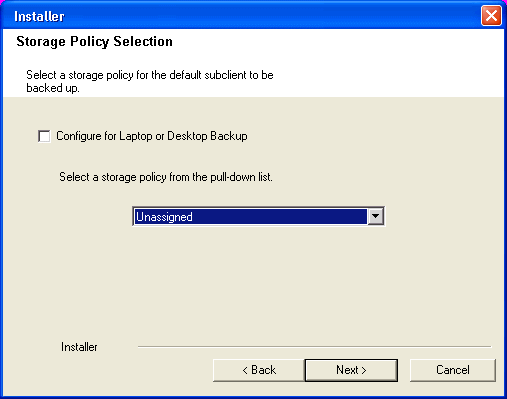
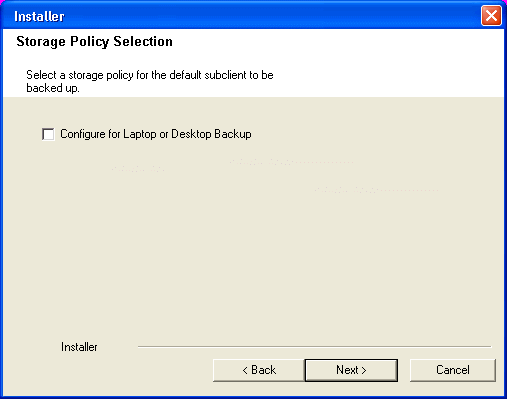
| 16. | Select a Storage Policy. Click Next. |
 |
||
| If you do not have Storage Policy created, this message
will be displayed. Click OK.
|
 |
|||
|
||||
Configure Exchange Database Specific Information |
||||
| 17. |
Select the backup type for Exchange Database backups. Choose either of the
following options, then click Next.
|
 |
||
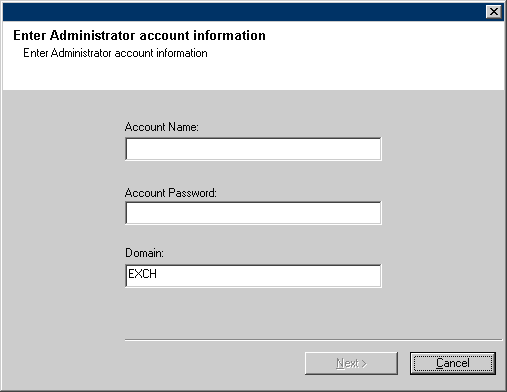
| 18. |
Enter the user credentials to access the Exchange Server to perform the backup
operation.
|
 |
||
| 19. | Click Next. |
 |
||
| 20. |
The install program displays a reminder to verify that Circular Logging is disabled before performing any database backup operations. To verify that Circular Logging is disabled:
Click OK. |
 |
||
|
||||
Configure Exchange Agents Specific Information |
||||
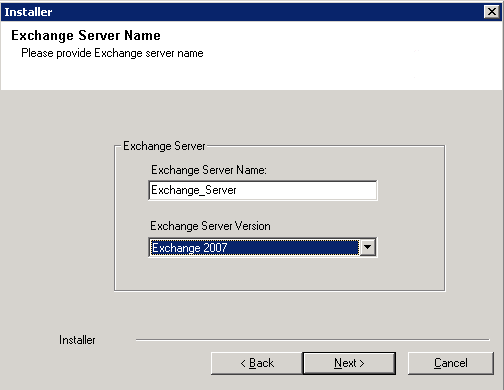
| 21. | Select Exchange Server Name and Exchange Server
Version from drop-down list. Click Next.
|
 |
||
| 22. | Click Next. |
 |
||
| 23. |
Enter the following Exchange Administrator information then
click
Next.
|
 |
||
Install Remaining Cluster Nodes |
||||
| 24. |
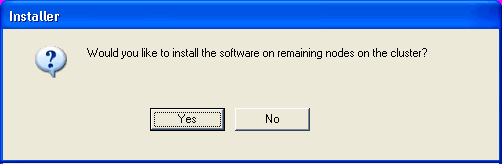
To install the software on the remaining nodes of the cluster, click Yes. To complete the install for this node only, click No. |
 |
||
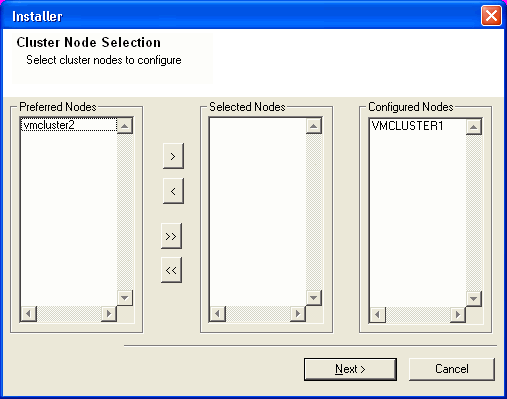
| 25. |
Select cluster nodes from the Preferred Nodes list and click the arrow
button to move them to the Selected Nodes list. Once you complete your selections, click Next.
|
 |
||
| 26. |
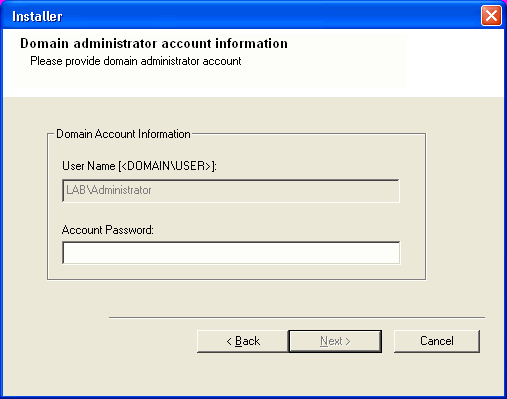
Specify User Name and Password for the Domain Administrator
account Information to perform the remote install on the cluster
nodes you selected in the previous step. Click Next. |
 |
||
| 27. |
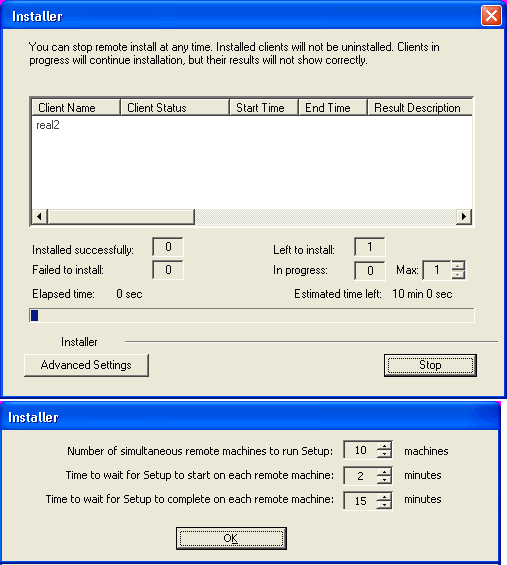
The progress of the remote install for the cluster nodes is displayed; the
install can be
interrupted if necessary.
Click Stop to prevent installation to any nodes after the current ones complete. Click Advanced Settings to specify any of the following:
|
 |
||
| 28. |
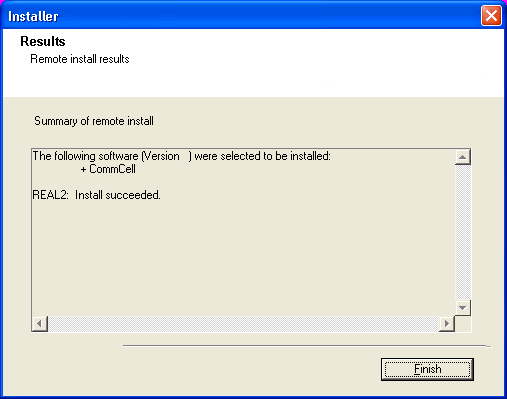
Read the summary for remote installation to verify that all selected nodes were installed
successfully. Click Next.
|
 |
||
| 29. | Click Next. |
 |
||
| 30. | Click Next. |
 |
||
| 31. | Click Finish. |
 |
||
 |
If you already have a storage policy selected in
step 16, Click
If you do not have Storage Policy created, continue with the following step. |
|||
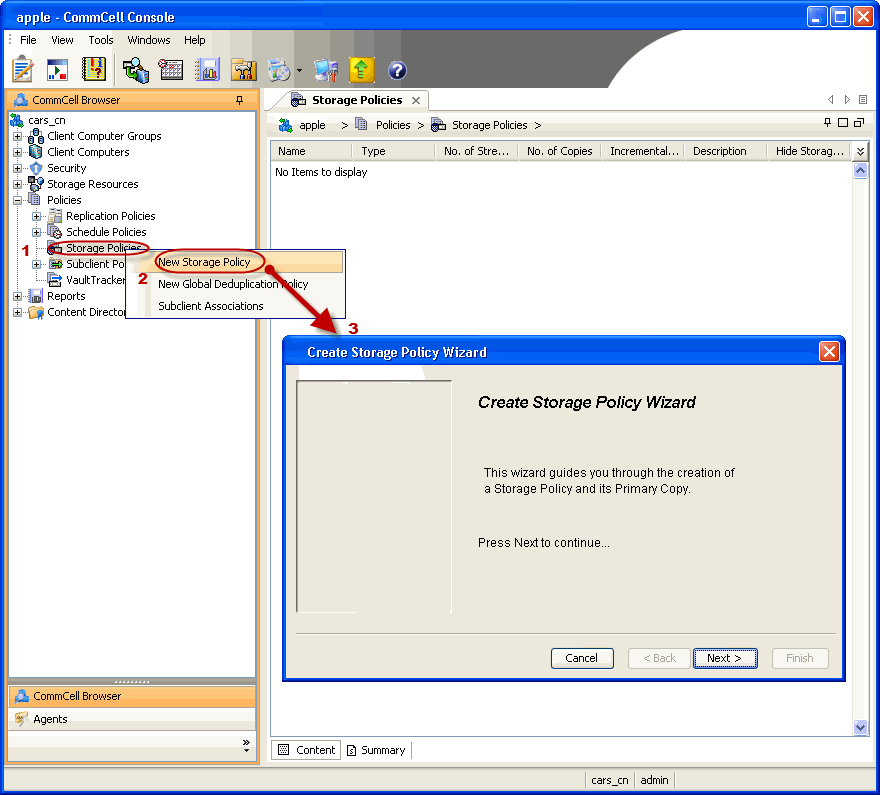
| 32. | Create a Storage Policy:
|
 |
||
| 33. |
Enable the following registry key to create job specific profiles:
|
|||
  |