Vulnerability Handling Policy
1 Reporting vulnerability
Eviden implements a responsible disclosure process that encompasses reporting Eviden’s products vulnerabilities.
Eviden investigates all reports regardless of the software code version or product lifecycle status. If the product has reached its End-of-Life, Eviden can decide to stop any further investigation at any time. A reported vulnerability will be processed through Product Security Incident Response.
2 Coordinated Vulnerability Disclosure
Vulnerability Statements are used in Coordinated Disclosure process to provide rapidly an information on whether Eviden products are potentially affected. They are usually gathered on Coordination Centers platforms such as [VINCE].
Eviden Security teams manage information related to vulnerabilities according to the Traffic Light Protocol (TLP 2.0) rules together with the general confidentiality obligations of Eviden’s security policies.
Throughout the investigative process Eviden strives to work collaboratively with the source of the report (incident reporter) to confirm the nature of the vulnerability, gather required technical information, and ascertain appropriate remedial action.
When the initial investigation is complete, results SHOULD be discussed with the incident reporter, as well as a plan for resolution and public disclosure.
During any investigation, Eviden manages all sensitive information on a highly confidential basis. Internal distribution is limited to those individuals who have a legitimate need to know and can actively assist in the resolution. Similarly, Eviden asks incident reporters to maintain strict confidentiality until complete resolutions are available for customers and have been published by Eviden through the appropriate coordinated disclosure.
Eviden works with third-party coordination centers such as [CERT-CC], or national CERTs to manage a coordinated industry disclosure for vulnerabilities that may impact multiple vendors (for example, a generic protocol issue). In those situations, Eviden either will assist the incident reporter in contacting the coordination center or may do so on its behalf.
Figure A - TLP 2.0 definitions (source: [CISA-TLP])
3 Vulnerability management lifecycle
Product Security Incident Response (PSIR) is the set of processes and resources Eviden puts in place to address vulnerabilities and defects related to Product Security. Eviden leverages the PSIRT Services Framework [FIRST-PSIRT] to implement its PSIRT capacity.
Eviden’s PSIR is organized in two consecutive phases: Neutralization and Remediation.
4 Assessing Security Risk using CVSS
Eviden uses version 3.1 of the Common Vulnerability Scoring System [FIRST-CVSS] to report potential vulnerabilities in its products. To indicate severity, the following guidelines are used.
|
Common Vulnerability Scoring System (CVSS) |
Overall score |
|||
|
Low |
Medium |
High |
Critical |
|
|
0.1-3.9 |
4.0-6.9 |
7.0-8.9 |
9.0-10.0 |
|
Figure B - CVSS 3.1 Qualitative Severity Rating Scale
To preserve consistency with its decision-making process, Eviden reserves the right to deviate from CVSS calculator [NVD-CVSS] on an exception basis if there are additional factors not properly captured in the usual way of computing CVSS score.
5 Vulnerability Neutralization
The neutralization phase is the decision-making process during which the risk posed by an incident is evaluated. The Stakeholder-specific Vulnerability Categorization (SSVC) is a system for prioritizing actions during vulnerability management promoted by CERT-CC [UCM-SSVC]. Eviden will leverage SSVC principles to determine its response priority. Eviden reserves the right to determine the type and degree of assistance it may offer in connection with any incident and to withdraw from any incident at any time, e.g., when the product has reached its End-of-Life.
Eviden may give priority consideration to security incidents that involve actual or potential threats to persons, property, or Critical Infrastructure Systems, as well as requests from law enforcement agencies or other incident response teams.
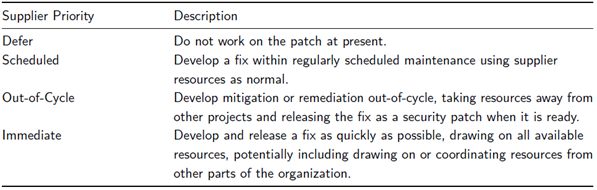
Figure C: Development Priority Outcomes (source: table 2 of [UCM-SSVC])
For clarity, there is no 1:1 mapping between CVSS scores and SSVC priority. A vulnerability rated at critical level under CVSS score can end with a Scheduled priority for its remediation.
6 Vulnerability Remediation
Before delivering a product firmware patch, some qualification tests SHALL be conducted by Eviden in conjunction with the customer. Delays are therefore mandatory to ensure a firmware update does properly fix a vulnerability.
7 Vulnerability Communication Policy
Beside the remediation decision, the outcome of Neutralization can be a Vulnerability Statement and/or a Security Bulletin.
A Vulnerability Statement usually links public vulnerabilities with a list of Eviden products and provides basic status for each product: known not affected, known affected, under investigation, or fixed.
8 Reward Policy
With the agreement of the incident reporter, Eviden may acknowledge the reporter’s contribution during the public disclosure of the vulnerability. Upon explicit request from the incident reporter, Eviden will respect the incident reporter’s anonymity.
Eviden offers no reward for responsible report of vulnerabilities on its products.
9 Security Bulletins
In a Security Bulletin, Eviden discloses the minimum amount of information to assess the impact of a vulnerability on an affected product and any potential steps needed to protect its environment. Eviden will try to suggest any solution, quick-fix, or workaround based on its knowledge, together with best-effort approach. “Currently no workaround available” is a valid statement in the context of the Neutralization phase. On a general basis, Eviden will not publicly disclose vulnerability details that could enable someone to craft an exploit before the end of the remediation phase. Eviden provides these security-related publications according to TLP rules.
10 References
|
[VINCE] |
|
|
[CERT-CC] |
|
|
[CISA-TLP] |
|
|
[FIRST-PSIRT] |
https://www.first.org/standards/frameworks/psirts/psirt_services_framework_v1.1 |
|
[FIRST-CVSS] |
|
|
[NVD-CVSS] |
|
|
[UCM-SSVC] |
https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=653459 |
11 Disclaimer
Although Eviden makes effort to provide accurate and complete information, Eviden shall not be liable for technical or editorial errors contained in its Security Bulletins. The information is provided “as is” without warranty of any kind. To the extent permitted by the Law, neither Eviden nor its affiliates, subcontractors or suppliers will be liable for incidental damages, downtime cost, lost profits, damages relating to the procurement of substitute products or services, or damages for loss of data, or software restoration.
The information in this document is subject to change without notice. Product and company names mentioned herein may be trademarks of their respective owners.
Last update: 19/01/2024
Any question related to this document can be sent to the Eviden PSIRT with the mention “Attn: Chief Product Security Officer”.
This document may have been altered due to its reproduction in the present system. The originally approved document is available upon request.