Choose from the following topics:
Related Topics:
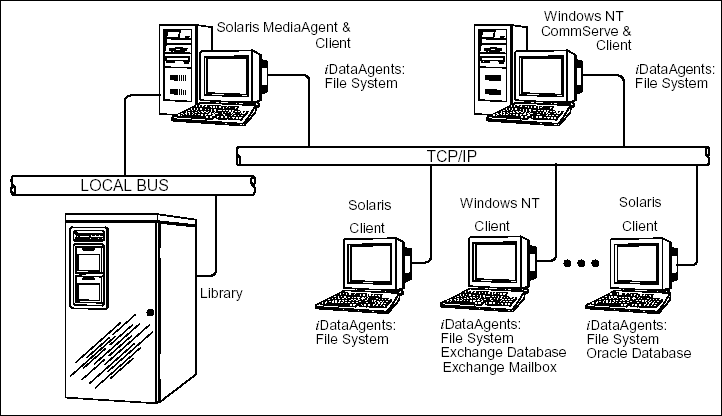
The Unix File Systems iDataAgents are backup and restore vehicles for file system data (i.e., files and directories) residing on Unix computer systems. These File System iDataAgents are just several of a group of iDataAgents that provide backup and restore support for different kinds of data in what is often a heterogeneous network environment. The following figure shows one such example (for the Solaris File System iDataAgent).
In general, each Unix File System iDataAgent except for the IRIX File System iDataAgent supports data protection operations for the appropriate Unix File System (UFS) data. In some cases, operations for some other File System data (e.g., CD-ROM File System [cdfs]) may be also supported. Also, some iDataAgents support additional file systems.
The Unix File System iDataAgents support the following file system types:
Supported File System(s) |
Unix File System iDataAgent(s) Providing Support |
| Advanced File System (advfs) | Tru64 |
| CD-ROM File System (cdfs) | All |
| Enhanced Journal File System (JFS2) | AIX |
| Extended 2 File System (ext2) | Linux |
| Extended 3 File System (ext3) | Linux |
| Extended 4 File System (ext4) | Linux |
| General Parallel File System (GPFS) | Linux |
| Hierarchical File System (HFS) | HP-UX |
| Journal File System (JFS) | AIX, HP-UX |
| Oracle Cluster File System (OCFS2) | Linux |
| Reiser File System (reiserfs) | Linux |
| Red Hat File System GFS 5.2 | Linux |
| Unix File System (UFS) | All except IRIX |
| VERITAS File System (VxFS) | AIX, HP-UX, Linux, Solaris |
| VERITAS Cluster File System (VxCFS) | AIX, HP-UX, Linux, Solaris |
| 'X' File System (XFS) | IRIX and Linux |
| Zettabyte File System (ZFS) | Solaris 10 6/06 64-bit only |
In addition, the following section and two tables provide specific information on the effect of supported data types on browses, backups and restores by the various Unix File System iDataAgents. The right-most column in each table provides references to the appropriate commentary, requirements, and/or restrictions for each scenario. If the reference is flagged by "*", be sure to check the referred section for further information if necessary.
For Browse operations involving On Demand backup sets, you can browse either a single symbolic link pointing to a raw device or the actual path leading to the device. You can also browse the same if the symbolic link points to one or more intermediate symbolic links and both the original link and the intermediate links are contents in the same subclient. However, if they are not part of the same subclient, you can browse only the contents of the symbolic link; you cannot browse the actual raw device data file in this case.
On the other hand, for Browse operations involving regular backup sets, you can browse only the symbolic link to the raw device that was provided as the subclient content during a backup; you cannot browse the path pointing to the actual raw device in this case. Under this scenario, you can browse the same if the symbolic link points to one or more intermediate symbolic links without regard as to whether the original link and the intermediate links are contents in the same subclient.
Effect of Data Types on Backups by Unix File System iDataAgents |
|||
| Backup Dispositions | Affected Data Types/Characteristics | Eligible Unix File System iDataAgents | References (*Requirements/*Restrictions) |
| Backups can be run successfully for: |
|
by any | *See Holed Files in Subclient Content. |
|
by Solaris | *See
Registry Keys: FileSystemAgent (nDUMPSIZE x); iDataAgent (nDUMPPERCENT x) |
|
|
by any except AIX | See Locked/Open Files. | |
|
by AIX, HP-UX, Linux and Solaris | *See Configure the Agent to Backup Raw Devices | |
|
by AIX, HP-UX, Linux and Solaris | *See Configure the Agent to Backup Raw Devices | |
|
by any | *See Handling Files With Non-ASCII Characters. | |
|
by Red Hat Linux AS 3.0 32-bit with kernel RH 2.4.21-15.ELsmp and glibc 2.3.2-95.20 (as guest OS/virtual machine) on VMware ESX Server | * See Back up VMware Virtual Machines. | |
|
by any | ||
| Backups cannot be run successfully for: |
|
by any except AIX | See Locked/Open Files. |
|
by any (with slight variation for AIX as noted) | See Maximum Filename Length for Unix File System iDataAgent Restores. | |
|
by HP-UX 11.00 vxfs File System on PA-RISC, and any version of Linux other than Red Hat Linux AS 3.0 and SuSE Linux Enterprise Server 9.0 | ||
|
by AIX, HP-UX, Linux and Solaris | ||
| Backups might not be run successfully for: |
|
by any | *See Backup Considerations. |
Effect of Data Types on Restores by Unix File System iDataAgents |
|||
| Restore Dispositions | Affected File Types/Characteristics | Eligible Unix File System iDataAgents | References (*Requirements/*Restrictions) |
| Restores can be run successfully for: | |||
|
by any | *See Restore Data - Unix File System. | |
|
|||
|
by AIX, HP-UX, Linux and Solaris | *See Restore Unix Raw Devices. | |
|
by AIX, HP-UX, Linux and Solaris | *See Restore Unix Raw Devices. | |
|
by any | *See Handling Files With Non-ASCII Characters. | |
|
by Red Hat Linux AS 3.0 32-bit with kernel RH 2.4.21-15.ELsmp and glibc 2.3.2-95.20 (as guest OS/virtual machine) on VMware ESX Server | *See Restore VMware Virtual Machines. | |
|
by any | See Restore Macintosh File System Resource Fork Data. | |
| Restores cannot be run successfully for: |
|
by HP-UX vxfs File System on PA-RISC, and any version of Linux other than Red Hat Linux AS 3.0 and SuSE Linux Enterprise Server 9.0 | |
|
by any | See Restore Data - Unix File System. | |
|
|||
|
by any (with slight variation for AIX as noted) | See Maximum Filename Length for Unix File System iDataAgent Restores. | |
| Restores should not be run for: |
|
by Tru64 | See Restore Data - Unix File System. |
|
by any except HP-UX | ||
| Restores might not be successfully run for: |
|
by any (with slight variation for AIX as noted) | See Maximum Filename Length for Unix File System iDataAgent Restores. |
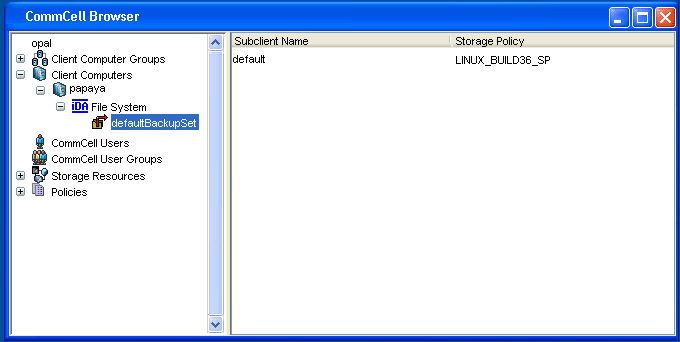
When the Unix File System iDataAgent is installed, the following levels are automatically created in the CommCell Browser.
 |
|
|
papaya:
Client File System: Agent defaultBackupSet: Backup Sets |
default: Subclients |
To perform a data protection operation using this Agent a specific Product License must be available in the CommServe® Server.
Review general license requirements included in License Administration. Also, View All Licenses provides step-by-step instructions on how to view the license information.
Holed files are files that, while not using large blocks of memory for actual data, do use empty blocks, inflating the file size. These files can be backed up. However, when they are restored, the size of empty blocks may not be the same as before. See also Backup Considerations for This Agent.