Replication Configuration
Topics |
How To |
Related Topics
Overview
Replication Scenario
Throttling
Orphan Files
Fan-In Recovery Points
Best Practices
Workstation Backup Agent uses ContinuousDataReplicator on the destination
computer to manage the backup data secured from the Workstation Agent source.
Managing the backup data includes, creating recovery points to access
point-in-time data, and back up the recovery points for future access. This
document explains the configurations required in the destination computer and
other replication options required for the successful data protection operations
using Workstation Backup Agent.
Workstation Backup source computers are configured to the destination
computer in a Fan-In configuration setup.
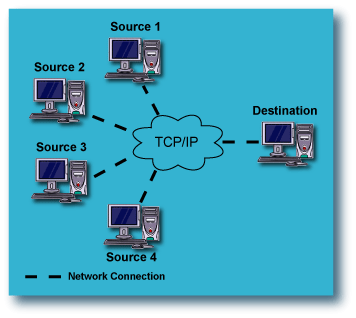
Fan-In: Replication from multiple Source computers to
a single Destination computer:
|
In a Fan-In configuration, multiple computers on the LAN or WAN have their data
replicated to a single computer, either local or remote. This provides
protection of all of the source computers against catastrophic failure, while
maximizing the use of resources by directing all the data to a single
destination computer.
On Windows, most of the configuration of replication and Recovery Point
options can be accomplished from the
Fan-In tab of the Agent Properties on the destination
computer, and these settings are automatically applied to all the source
computer. On UNIX, replication and Recovery Point options must be
configured on each source computer.
Scalability
Although the scalability of a Fan-In setup can vary based on network and system
resources, it is recommended that each Fan-In setup contains no more than 100
source clients.
For maximum performance and robustness, the total number of Replication Pairs
configured for the same source volume should be kept to a minimum. If multiple
Replication Pairs must be configured for the same source volume, the recommended
upper limit is five.
For more information, see
Using
ContinuousDataReplicator in a Fan-In Configuration.
|
 |
You can configure several throttling options at the
Agent level, in the
Operational Parameters
tab of the agent properties screen.
The following can be configured on the Source computer:
- Throttling Amount - maximum network transfer rate in megabits per
second (Mbps).
On Windows, the setting for Throttling Amount will apply to each pipeline engaged in replication
activity, not the aggregate of all pipelines for all Replication Pairs on the
computer. With respect to the number of pipelines that will be active at any
one time, review the following based on an example of having a Throttling Amount setting
of 10Mbps:
- Each Replication Pair requires a pipeline during Baselining or
SmartSync; if you have
3 Replication Pairs in the SmartSync phases at the same time, you have 3
pipelines active, and thus a 30Mbps maximum network transfer rate for
the source client (3 pipelines at 10Mbps each.) After Baselining and
SmartSync have completed
for each Replication Pair, only 1 pipeline will remain in use, and the maximum
network transfer rate will be reduced to 10Mbps.
- Fan-Out configurations require a pipeline for each destination client;
if you have 5 Replication Sets configured to replicate data to 5 clients,
you have 5 pipelines active, and thus a 50Mbps maximum network transfer
rate for the source client (5 pipelines at 10Mbps each.)
- Other than the cases listed, Baselining or SmartSync, and Fan-Out, all other
replication activity will require 1 pipeline, and thus the Throttling Amount
specified will apply to the aggregate of all activity on the source
computer, comprised of the replication activities of all Replication Pairs.
On UNIX, the setting for Throttling Amount will apply to the aggregate of all pipelines for all Replication Pairs on the
computer. With respect to the number of pipelines that will be active at any
one time, review the following based on an example of having a Throttling Amount setting
of 30Mbps:
- Each Replication Pair requires a pipeline during Baselining or SmartSync; if you have
3 Replication Pairs in the SmartSync phases at the same time, you have 3
pipelines active, which will equally divide the specified 30Mbps maximum
network transfer rate for the source client, for a maximum rate of 10Mbps
each. After Baselining and SmartSync have completed for each Replication
Pair, only 1 pipeline will remain in use, and the maximum network transfer
rate of 30Mbps will apply to that pipeline.
- Fan-Out configurations require a pipeline for each destination
client; if you have 5 Replication Sets configured to replicate data to 5
clients, you have 5 pipelines active, which will equally divide the
specified 30Mbps maximum network transfer rate for the source client,
for a maximum rate of 6Mbps each.
If your destination computer is serving that function for multiple source
computer, you may need to set this limit on each of the source computers, such
that the destination computer has sufficient time for log replay from all source
computers. Note that the Throttling Amount must be specified first, before you
can create Bandwidth Throttling Rules (see next item.)
- Bandwidth Throttling Rules - scheduled network throttling, specifying
a time range, and a percentage of maximum transfer rate, specified as the Throttling Amount, during that time range.
Once again, the limit set here will apply to the aggregate of all activity on the source computer, comprised of the replication activities of all Replication
Pairs. This setting allows you to select high and low (or no) activity periods
in a manner similar to the 'operation window' concept used when scheduling the
activities of job-based Agents.
 |
- When configuring throttling, you should consider what unintended affects
throttling might have on operations. As one example, if you have a source computer
that has significant file write activity, and you impose network bandwidth throttling
which makes it impossible to transfer the logs quickly enough to the destination
computer to keep pace with the rate of change on the source computer, log file
space requirements would increase dramatically on the source computer. In such
a case, provision must be made for sufficient log file space, based on the expected
activity and throttling.
- An example of a beneficial use of throttling involves configurations where
multiple source computers are all configured to use the same destination computer.
In this case, you may want to impose throttling on the source computers to allow
the destination computer enough time to keep pace with all the log files it
is receiving, and ensure sufficient log space on the destination computer as
well to accommodate all of the logs it will be receiving.
- You can configure Alerts to be generated when throttling is imposed, or
when 80 percent or more of a volume's disk space is consumed, for all of the
client computer's volumes. For more information, see
Alerts and Monitoring.
- On Windows in a clustered environment, when a cluster node is
the active node for more than one virtual server at the same time,
throttling rules are applied equally to all of the virtual servers hosted by
that physical node, using
the highest numbers specified for any one of them. For example, consider an
active node hosting three virtual servers simultaneously, with throttling
configured as follows on each of the virtual servers, VS1, VS2, and VS3:
| Throttling Parameter |
VS1 |
VS2 |
VS3 |
| Throttling based on percentage of free log
space on destination: |
30% |
35% |
40% |
| Stop
replication based on percentage of free log space on
destination: |
80% |
70% |
60% |
| Abort source based on percentage of free log space
on source: |
75% |
80% |
70% |
|
Network Bandwidth Throttling amount: |
10Mbps |
40Mbps |
90Mbps |
Since throttling for all Virtual Servers will be based on the
highest number specified for any one of them, all three Virtual
Servers would be subject to the throttling numbers shown in bold, not
necessarily the numbers specified individually. If throttling is imposed
based on the destination computer running low on log space, in this example,
when free log space reaches 40% on any virtual server, the maximum transfer
rate will be reduced by 50% on each of the virtual servers -- to 5Mbps on
VS1, 20Mbps on VS2, and 45Mbps on VS3.
|
For step-by-step instructions, see
Configure Network Bandwidth Throttling.
Files that are in the destination directory, but not the source directory,
are orphan files. You can choose to ignore, log, or delete such files that are
identified in the destination path; these settings are configured in the Orphan
Files tab of the Replication Set Properties.
By default, the Orphan File Processing is turned off and the orphan files are
moved from the destination directory to another location and are available for
restore. You can select the Show Deleted Items option in the browse screen to
view and restore orphan files.
To configure Orphan File settings, see
Configure Orphan File Processing
for step-by-step instructions.
To view Orphan Files, see
View
Orphan Files for step-by-step instructions.
- A file that is created on the source and is then deleted before it has been
replicated, will still be created on the destination and then deleted. This
is because both the creation and deletion of the file are captured in the log
file, and this will be replayed on the destination computer. These are not treated
as Orphan Files.
- A renamed file will be replicated to the destination as a new file. The
previous copy with the old name will remain on the destination and be treated
according to your Orphan Files settings.
- If you change the orphan file settings for an existing Replication Set,
the change will only affect Replication Pairs that are created after the change,
or Replication Pairs that are aborted and restarted. Currently active Replication
Pairs will not be affected by the change until they are aborted and restarted.
- It is strongly recommended that you do not replicate to the root of the
destination client or the filer volume. If for any reason you need to
replicate to the root of the volume then ensure that the Orphan File
Processing is turned off from the Replication Set Properties.
See Restore Deleted
Items to restore Orphan Files.
Fan-In Recovery Points consist of snapshots of a Destination Path, created to
preserve a point-in-time data on the destination computer in a Fan-In
configuration. Snapshot-based Recovery Points can be created,
and backed up, affording additional data protection options for recovery of your
data. In addition, Recovery Points can be mounted, and for Windows can also be
shared, and thus made available to users on the network.
Recovery Points consist of snapshots created on the
destination computer by the specified snapshot engine, without any reference to the state of the source computer.
It simply represents a point-in-time on the destination computer, and is thus
more useful for file system data than for application data. To use Recovery Points, see the following for step-by-step procedures:
Recovery Points can be configured to be backed up automatically when
they are created. In
addition, you can select any existing Recovery Point and perform an immediate
full backup on-demand. This
backup capability is only available if the source and destination computers have the
appropriate File System iDataAgent
installed. For more information about installing, configuring, and using File System iDataAgents, see
Windows File System.
The following types of backups are supported:
- Full
- Differential
- Incremental
- Synthetic Full
See the following for step-by-step procedures:
When the maximum number of Recovery Points is reached, based on the maximum
number you specified, or based on the
maximum number of recovery points
allowed by the system, they are automatically deleted by the system in the
order they were created (oldest first) unless one of the Recovery Points to be
deleted is in use.
Recovery Points can also be deleted manually. For step-by-step procedures, see
Delete a
Fan-In Recovery Point Using CDR.
You can specify commands to run either before a Recovery Point is created
and/or after a Recovery Point is created. For general information about Pre/Post
commands, see Pre/Post Processes.
See the following for step-by-step
procedures for Pre/Post Processes:
- If destination path is UNC path., then Recovery Point creation is not
possible.
- ONTAP Fan-In Recovery Points are not supported.
It is recommended that you keep the following in mind when performing
data replication:
- Destination volume size: ensure
that the destination volume has sufficient space for all the data that will
be replicated to it. If you are replicating data from multiple source
volumes to the same destination volume (Fan-In), ensure that the destination
volume is sufficiently large for the data which will be replicated from all
the source volumes. If you are creating Recovery Points, you must also
account for the space requirements of the snapshots that will be created on
the Destination.
- Individual failed files or folders will not necessarily fail the replication job. Such
individual failures may just be logged and the data replication job will continue.
Check the logs periodically for such failures. See
View
the Log Files of an Active Job.
- Replication performance on Windows - to increase the speed at which data is replicated,
the pipeline buffer size can be reconfigured from the default size of 64KB up
to a maximum of 256KB (in increments of 32KB) using the
PipelineBufferSizeInKiloBytes
registry key. However, if the value of this key is set too high combined
with a low kernel memory the operation may fail because the system lacks
sufficient buffer space or because a queue was full.
- For Windows, when communication is interrupted between the source and destination computers,
the source computer will make 30 attempts (this default number can be changed
using the
MaxConnectionAttempts
registry key) to reconnect to the pipeline, after which the Replication Pair(s)
will show a state of Failed. Each connection attempt takes several minutes,
an interval which is neither programmatic nor configurable.
- For Windows, the virtual memory paging file (pagefile.sys)
must be configured on a local, fixed disk.
-
For Windows, the
nDoNotReplicateACLs registry key can be used to disable the
replication of the security security stream of files. This stream includes user
and group access control list (ACL) settings for file access. If this registry
key is not present, ACLs will be replicated.
Back to Top
