Remote Backup
Topics |
How To |
Support |
Related Topics
Overview
Supported Data Types
Supported Configurations
Use of Snapshots
License Requirements
Installation
Configuration
Operations
Other Configurations
Notes and Considerations
Best Practices
Remote Backup is a light-weight solution to maintain application and file
system data in a remote backup location. Remote Backup uses an ingenious design
to identify the precise changes to the data protected on the source, and
transfers only the modified data to the remote backup. This reduces the data
transferred over the network enabling faster backup cycles. Remote backup
operations can be performed at any desired time, providing control on the use of
network. The schedulable backup operation allows you to strategize network usage
and this significantly benefits the system performance.
Application data can be
protected in a consistent state, and restored to point-in-time upon
recovery. See Application Integration for
more details. Remote Backup solution is best suited for protecting highly dynamic
application data without compromising system performance. Source data can be
compressed and encrypted during the backup for efficiency and data security.
Remote Backup also verifies the integrity of data during the transfer, providing
additional security.
The backup data on the destination can be moved to secondary storage, and
still restored back to the source when required.
The backup data on the
destination also supports offline mining for Active Directory and Exchange data. See
Exchange Offline Mining
and
Active Directory Offline Mining
for details on offline mining.
Data protection operations for the data types listed below are supported for
Remote Backup.
Windows File Systems
- New Technology File Systems (NTFS)
- Access Control Lists (ACL)
- Unicode files
- Sparse files (except where the destination is a NetApp filer)
- Single Instance Storage
- Mount Points
- Encrypted files (except where the destination is a NetApp filer)
- Shared Volumes
- Compressed Data (except where the destination is a NetApp filer) - including a compressed file contained in a compressed
folder, any folder (not compressed) that contains two or more compressed files,
or a compressed drive.
- Dynamic volumes are supported as Replication Pair content
- Software and Hardware RAID storage
- Migration files (stub only)
 |
- When replicating a root volume (e.g., C:\),
paging files, the System Volume folder, and the hibernation files will be
filtered out automatically from Replication Pair content, and will not be
replicated to the destination machine.
- It is recommended that you use recovery points on the destination for
examining consistency of data on a destination computer, as comparing
live data on source and destination may result in the files not matching.
- Also refer to
Application Integration.
-
For a complete listing of applications supported for each operating system, see
Application - Support.
|
Unix File Systems
- Logical volumes for AIX and Linux; only Linux supports file systems on physical disks
configured as CXBF devices
- Access Control Lists (ACL)
- Unicode files; files with non-ASCII characters in their name
- Sparse files (during data replication phase only; see Note below)
- Migration files (stub only)
- Linux only:
- Extent 2 File System (ext2)
- Extent 3 File System (ext3)
- Reiser File System (reiserfs)
- VERITAS File System (VxFS)
- AIX only:
- Enhanced Journaled File System (JFS2)
- VERITAS File System (VxFS)
- Solaris only:
- Zettabyte File System (ZFS)
- Unix File System (UFS)
- VERITAS File System (VxFS)
 |
- File system directories as
/, /usr,
/var, /tmp
are not backed up.
-
On Linux, we only support VERITAS File System (VxFS) on volumes
created by Veritas Volume Manager.
- On Unix, sparse files
are backed up as regular files.
-
For a complete listing of applications supported for each operating system,
see Application - Support.
|
Common scenarios for setting up the Remote Backup solution are illustrated below, but these
by no means illustrate all of the ways in which it can be configured.
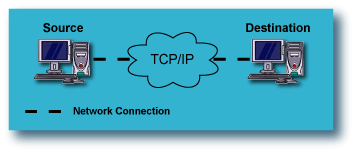
Remote Backup from one Source computer to one Destination computer:
|
This is the most fundamental configuration for data replication. A single
computer on the LAN or WAN has its data replicated to another computer,
either local or remote. This provides protection of the source
computer against catastrophic failure of the computer itself.
|
 |
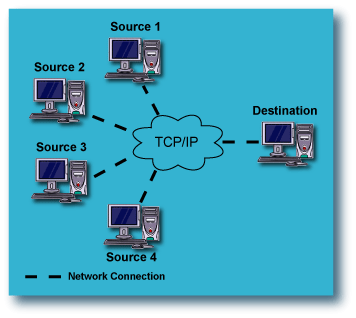
Fan-In Configurations: Remote Backup from multiple Source computers to
a single Destination computer:
|
In a Fan-In configuration, multiple computers on the LAN or WAN have their data
replicated to a single computer, either local or remote. This provides
protection of all of the source computers against catastrophic failure, while
maximizing the use of resources by directing all the data to a single
destination computer.
On Windows, most of the configuration of replication and Recovery Point
options can be accomplished from the
Fan-In tab of the Agent Properties on the destination
computer, and these settings are automatically applied to all the source
computer. On UNIX, replication and Recovery Point options must be
configured on each source computer.
Scalability
Although the scalability of a Fan-In setup can vary based on network and system
resources, it is recommended that each Fan-In setup contains no more than 100
source clients.
For maximum performance and robustness, the total number of Replication Pairs
configured for the same source volume should be kept to a minimum. If multiple
Replication Pairs must be configured for the same source volume, the recommended
upper limit is five.
|
 |
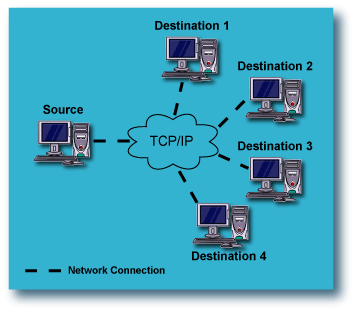
Fan-Out Configurations: Remote Backup from one Source computer to multiple
Destination computers:
|
This configuration for data replication, referred to as "Fan-Out", adds
significantly to the protection afforded to the source computer, because
of the redundancy. A single computer on the LAN or WAN has its data replicated
to multiple computers, any of which can be either local or remote. This
provides protection against catastrophic failure of an entire
site, as well as the source computer itself. |
 |
The following snapshots engines are supported for creating snapshots on the
destination computers in the Remote Backup configuration:
This feature requires a Feature License to be available in the CommServe® Server.
Review general license requirements included in
License Administration. Also,
View All Licenses provides step-by-step
instructions on how to view the license information.
- Requires ContinuousDataReplicator product license on the source
and destination computers.
- Requires Recovery Point feature license on the destination
computer for using the Recovery Point feature.
Install the latest version of ContinuousDataReplicator on the source and
destination computers. See Deployment -
ContinuousDataReplicator for the installation procedure. Review
System Requirements - Continuous
Data Replicator for supported platforms. No special
configuration is required during the installation.
Application data is automatically configured by discovering directories that
should be backed up (logs, databases, etc.) to protect supported applications.
See Application - Support
for the list of applications supported for Remote Backup. Supported app
For applications that are
not supported, data consistency in the backup can be achieved quiesced during the backup to achieve consistence
point-in-time data for Backup.
Integrated Applications:
Integrate the applications at the agent level and use the Add App
feature to add Replication Pairs containing application data. See
Application - Support for
supported applications.
Non-Integrated Applications:
For applications that are not natively supported, customized user-defined
scripts can be used to quiesce the applications during backup.
For applications that use VSS writers, you can engage all VSS writers
to capture data in a consistent state during the backup. Use the Engage All VSS
Writers
option in the
Manage Pairs dialog box.
Also, if there are multiple applications in the source volume and the data
traffic on those applications would affect the data capture for backup, then
using this option would engage all the VSS writers and enable data capture.
You can configure network throttling options at the
Agent level, in the
Operational Parameters tab of the agent Properties screen. See
Configure Network Bandwidth Throttling for
instructions.
The following can be configured on the Source computer:
- Throttling Amount - maximum network transfer rate in megabits per
second (Mbps).
On Windows, the setting for Throttling Amount will apply to each pipeline engaged in replication
activity, not the aggregate of all pipelines for all Replication Pairs on the
computer. With respect to the number of pipelines that will be active at any
one time, review the following based on an example of having a Throttling Amount setting
of 10Mbps:
- Each Replication Pair requires a pipeline during Baselining or
SmartSync; if you have
3 Replication Pairs in the SmartSync phases at the same time, you have 3
pipelines active, and thus a 30Mbps maximum network transfer rate for
the source client (3 pipelines at 10Mbps each.) After Baselining and
SmartSync have completed
for each Replication Pair, only 1 pipeline will remain in use, and the maximum
network transfer rate will be reduced to 10Mbps.
- Fan-Out configurations require a pipeline for each destination client;
if you have 5 Replication Sets configured to replicate data to 5 clients,
you have 5 pipelines active, and thus a 50Mbps maximum network transfer
rate for the source client (5 pipelines at 10Mbps each.)
- Other than the cases listed, Baselining or SmartSync, and Fan-Out, all other
replication activity will require 1 pipeline, and thus the Throttling Amount
specified will apply to the aggregate of all activity on the source
computer, comprised of the replication activities of all Replication Pairs.
On UNIX, the setting for Throttling Amount will apply to the aggregate of all pipelines for all Replication Pairs on the
computer. With respect to the number of pipelines that will be active at any
one time, review the following based on an example of having a Throttling Amount setting
of 30Mbps:
- Each Replication Pair requires a pipeline during Baselining or SmartSync; if you have
3 Replication Pairs in the SmartSync phases at the same time, you have 3
pipelines active, which will equally divide the specified 30Mbps maximum
network transfer rate for the source client, for a maximum rate of 10Mbps
each. After Baselining and SmartSync have completed for each Replication
Pair, only 1 pipeline will remain in use, and the maximum network transfer
rate of 30Mbps will apply to that pipeline.
- Fan-Out configurations require a pipeline for each destination
client; if you have 5 Replication Sets configured to replicate data to 5
clients, you have 5 pipelines active, which will equally divide the
specified 30Mbps maximum network transfer rate for the source client,
for a maximum rate of 6Mbps each.
If your destination computer is serving that function for multiple source
computer, you may need to set this limit on each of the source computers, such
that the destination computer has sufficient time for log replay from all source
computers. Note that the Throttling Amount must be specified first, before you
can create Bandwidth Throttling Rules (see next item.)
- Bandwidth Throttling Rules - scheduled network throttling, specifying
a time range, and a percentage of maximum transfer rate, specified as the Throttling Amount, during that time range.
Once again, the limit set here will apply to the aggregate of all activity on the source computer, comprised of the replication activities of all Replication
Pairs. This setting allows you to select high and low (or no) activity periods
in a manner similar to the 'operation window' concept used when scheduling the
activities of job-based Agents.
 |
- When configuring throttling, you should consider what unintended affects
throttling might have on operations. As one example, if you have a source computer
that has significant file write activity, and you impose network bandwidth throttling
which makes it impossible to transfer the logs quickly enough to the destination
computer to keep pace with the rate of change on the source computer, log file
space requirements would increase dramatically on the source computer. In such
a case, provision must be made for sufficient log file space, based on the expected
activity and throttling.
- An example of a beneficial use of throttling involves configurations where
multiple source computers are all configured to use the same destination computer.
In this case, you may want to impose throttling on the source computers to allow
the destination computer enough time to keep pace with all the log files it
is receiving, and ensure sufficient log space on the destination computer as
well to accommodate all of the logs it will be receiving.
- You can configure Alerts to be generated when throttling is imposed, or
when 80 percent or more of a volume's disk space is consumed, for all of the
client computer's volumes. For more information, see
Alerts and Monitoring.
- On Windows in a clustered environment, when a cluster node is
the active node for more than one virtual server at the same time,
throttling rules are applied equally to all of the virtual servers hosted by
that physical node, using
the highest numbers specified for any one of them. For example, consider an
active node hosting three virtual servers simultaneously, with throttling
configured as follows on each of the virtual servers, VS1, VS2, and VS3:
| Throttling Parameter |
VS1 |
VS2 |
VS3 |
| Throttling based on percentage of free log
space on destination: |
30% |
35% |
40% |
| Stop
replication based on percentage of free log space on
destination: |
80% |
70% |
60% |
| Abort source based on percentage of free log space
on source: |
75% |
80% |
70% |
|
Network Bandwidth Throttling amount: |
10Mbps |
40Mbps |
90Mbps |
Since throttling for all Virtual Servers will be based on the
highest number specified for any one of them, all three Virtual
Servers would be subject to the throttling numbers shown in bold, not
necessarily the numbers specified individually. If throttling is imposed
based on the destination computer running low on log space, in this example,
when free log space reaches 40% on any virtual server, the maximum transfer
rate will be reduced by 50% on each of the virtual servers -- to 5Mbps on
VS1, 20Mbps on VS2, and 45Mbps on VS3.
|
Create a Replication Set on the source computer with the
Replication Type - Remote Backup. See
Create a Replication Set for
step-by-step instructions. See Replication Set
for more discussions on Replication Sets.
Consider the following options
while creating the Replication Set:
- In the
Replication Options tab, select the snapshot engine for creating
Recovery Points on the destination.
- On Unix platforms, in the Replication Set
General tab, select one of the following options:
- Specify compression of replicated data on the network. For
more information, see
Replication
Compression.
- Specify encryption of replicated data on the network. For
more information, see
Replication
Encryption.
- Specify how Orphan Files will be handled, when discovered on the destination
computer. For more information, see Orphan Files. By
default, orphan file processing for the replication set is turned Off.
- Specify files, folders, and patterns to be excluded from data
replication activities. For more information, see
Replication Filters.
Files that are in the destination directory, but not the source directory,
are orphan files. You can choose to ignore, log, or delete such files that are
identified in the destination path; these settings are configured in the Orphan
Files tab of the Replication Set Properties.
To configure Orphan File settings, see
Configure Orphan File Processing
for step-by-step instructions.
- A file that is created on the source and is then deleted before it has been
replicated, will still be created on the destination and then deleted. This
is because both the creation and deletion of the file are captured in the log
file, and this will be replayed on the destination computer. These are not treated
as Orphan Files.
- A renamed file will be replicated to the destination as a new file. The
previous copy with the old name will remain on the destination and be treated
according to your Orphan Files settings.
- If you change the orphan file settings for an existing Replication Set,
the change will only affect Replication Pairs that are created after the change,
or Replication Pairs that are aborted and restarted. Currently active Replication
Pairs will not be affected by the change until they are aborted and restarted.
- It is strongly recommended that you do not replicate to the root of the
destination client or the filer volume. If for any reason you need to
replicate to the root of the volume then ensure that the Orphan File
Processing is turned off from the Replication Set Properties.
Create Replication Pairs to the replication sets. See
Add or
Edit a Replication Pair for step-by-step instructions to add the replication
pairs. See
Replication Pair for more
details.
Replication Pairs are designated set of data on the source computer
configured for backup. Replication pairs can contain application data and/or
file system data. If your Replication Pair contain application data, then consider the following options
while creating the Replication Pairs:
- For supported applications, use the Add App option to add the
pair details.
- For applications that use VSS writers, select the Engage All VSS Writers option to
ensure consistent backup. See
Application Integration for more
details.
Replication Policies provide a template for replication sets. If you have a
multiple Replication Sets with common configurations, you might want to use
create a Replication policy, and use the policy to create the Replication Sets.
See Replication Policy
for more details.
The following operations can be performed using Remote Backup.
Remote Backup operations are performed at the Replication Set level. The contents of all
the Replication Pairs in the Replication Set are backed up to the destination computer.
Remote Backup supports two types of backup operations, Full and Incremental. For more
information on Full Backup, see Full Backups.
For more information on Incremental Backup, see
Incremental Backups.
In cases where the initial backup involves transferring large amounts of data
from the Source computer to the Destination computer, and the
network connection does have the bandwidth to transfer the data, you can seed the initial data using alternative data transfer
methods. Once the initial data transfer is complete, you can continue with the
traditional backup for subsequent incremental backups. See
Transfer Data When a Full Backup Cannot be Performed
for step-by-step instructions.
Recovery Points are snapshots (point-in-time copy) of the backup data on
the destination computers. Recovery Points can be created, and backed up,
affording additional data protection options for recovery of your data. In
addition, Recovery Points can be mounted, and for Windows can also be shared,
and thus made available to users on the network.
Recovery Point creation must be configured at the Replication Set level. See
Configure CDR Recovery Points
for instructions.
The following types of Recovery Points can be created for Remote Backup
operations:
Consistent Recovery Points
A Consistent Recovery Point defines a point-in-time where data is in a
consistent state on the source computer, ensuring the data can be restored to
that point-in-time; this is more useful for application data than for file
system data.
Remote Backup provides the following options to create consistent Recovery Points in the
destination .
- Create Recovery Points on demand. Right-click the Replication Set, and
select the option Create Recovery Point. This creates a Recovery
Point at the destination volume containing backup data.
See Create a Recovery Point Using CDR
for instructions. On-demand Recovery points creation and Remote Backup
operations are mutually exclusive, thus ensuring the consistency Recovery
Points on the backup data.
- Create Recovery Points at the end of the backup job. When the Remote
Backup is performed using Quiesce Applications option, then Recovery
Points created at the end of the backup job are consistent Recovery Points.
See e Start a Full/Incremental Backup
for instructions.
Fan-In Recovery Points
Fan-In Recovery Points consist of snapshots created on the destination
computer (configured in Fan-In setup) by the specified snapshot engine, without
any reference to the state of the source computer; this is suitable for file
system data.
Backup Recovery Point
Recovery points can be backed for additional protection, and more data
recovery options. See
Backups of Recovery Points
complete details.
Mounting or Sharing Recovery Point Snapshots
Recovery Points can be mounted, and for Windows can also be shared, and thus
made available to users on the network. See
Mounting or Sharing Recovery Point Snapshots
for complete details.
You can browse the destination to view the Live Copy of backup data, and to
view the Recovery Points that have been created for the Replication Set(s). The
browse option can be invoked from the Client, Agent, Replication Set, or
application iDataAgent level; see
Browse Data for the
complete set of browse options available at each level.
Data backed up from the source computer to the destination computer can be
recovered back using one of the following
Recovery
Scenarios:
Copy Back from Recovery Point or Destination Computer
A Copyback operation copies the contents of a destination path (Live Copy) or
Recovery Point to a specified recovery host and recovery path. This is true for
both file system data, as well as application data. The Live Copy or multiple Recovery Points
can be copied back by selecting them during the browse,
and then specifying the destination for the
copyback operation. Copyback can be performed from any of the levels
described in Browse Data. See
Copyback for more
details.
Use the following procedures to copy back from the destination computers:
- For file system data, use
Copy Back File System Data from a Recovery Point
or the Live Copy.
- For Exchange data, use
Copy Back Exchange Data from
a Consistent Recovery Point.
- For SQL data, use
Copy Back SQL Data from a
Consistent Recovery Point.
- For Oracle data, use
Copy Back
Oracle Data from a Consistent Recovery Point.
Mount or Share Recovery points
Recovery Points can be mounted on the destination computer,
or for Windows they can also be shared from the destination
computer, and thus made available to users on the network. For more information,
see
Mounting or Sharing Recovery Point Snapshots.
For step-by-step procedures, see the following:
Restore Data from Backup
The backup of Recovery Points or Consistent Recovery Points is performed
using the Windows File
System iDataAgent, which is also
used to perform restore operations. For more information about restoring from a
backup, see Restore Data - Windows File Systems.
Remote Backup jobs can be monitored and managed from the Job Controller. You
can view job information, and control the backup jobs from the job controller. Remote
office backup jobs are restartable; you can suspend and resume the backup jobs.
See Job Management for more information on monitoring
backup jobs from the Job
Controller.
Job History allows you to view more detailed information about a
job once it has completed. The following job histories are available for Remote
Backup:
The Job Summary Report allows you to review the details of the Remote Backup
jobs performed on this client. See
Job Summary Report for more details and access information.
If you wish to change an existing ContinuousDataReplicator
setup to use Remote Backup, see Switch from Continuous Replication to Remote Backup.
Review the following best practices when using the Remote Backup solution:
- If you are using the Remote Backup solution to backup application data, it
is recommended that you do not use Fan-In configuration.
-
For Windows, the
nDoNotReplicateACLs registry key can be used to disable the
replication of the security security stream of files. This stream includes user
and group access control list (ACL) settings for file access. If this registry
key is not present, ACLs will be replicated.
Back to Top


