Firewall Considerations
Topics |
How To |
Related Topics
Overview
Port-Based Firewall
Considerations
Application-Based Firewall
Considerations
Program-Based Firewall
Considerations
Firewalls provide security to networks by acting as a barrier for unauthorized
outside access to the network. Firewalls provide security by enforcing
restrictions on computers and applications communicating across it.
Typically a firewall divides the network into two parts which are broadly
referred to as secure/friendly side and the hostile side. CommCell components can be configured to function across a firewall when computers
hosting these components are located on different sides of firewall(s).
- Firewalls open only certain port numbers which in turn can be used by computers
located on the other sides of the firewall to communicate with each other.
In most common scenarios, the computers on the hostile side can communicate
with computers on the secure side using only a set of known or opened ports.
- Any network sessions that become idle beyond a pre-configured firewall timeout
period are automatically disconnected by the firewall, without providing a warning
to the applications.
- With a new connection, the firewall may transparently disconnect the connection,
if the application initiating the connection does not send its first communication
packet within a timeout period.
|
The following are the most commonly seen configurations in which the
CommCell components are located across a firewall:
- CommServe and MediaAgent are on the friendly side (also referred
as safe side), while
some or most of the agents are located on the hostile side (also
referred as public / DMZ side.
- Conversely, CommServe and MediaAgent are on the hostile side,
while some or most of the agents are located on the friendly side.
- CommServe is on the friendly side, while some or most MediaAgents
and agents are on the hostile side. (Some MediaAgents and agents may
even be on the same machine.)
- Conversely, CommServe is on the hostile
side, while some or most MediaAgents and agents are located on the friendly
side.
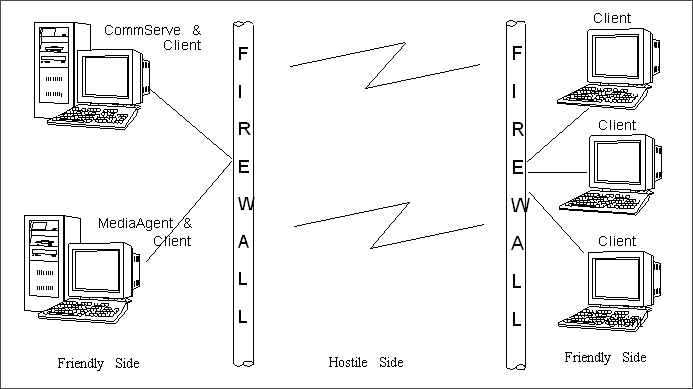
Keep in mind that these configurations may in fact be located behind
two firewalls because now there are two friendly sides to deal with.
The diagram on the right shows one such example.
|
 |
|
For products like ContinuousDataReplicator and
Workstation Backup, where the communication is between the CommServe,
destination computer (installed with ContinuousDataReplicator) and the corresponding agents,
then replace the
MediaAgent with destination computer in the above configurations.
The rest of the firewall considerations remain the same. This is
also applicable for MediaAgent Replication and Remote Backup
solutions. |
CommCell communication across firewall(s) can be configured using the Firewall
Configuration wizard.
Firewall services can be configured during the installation of CommCell
Components; the installation presents the firewall configuration wizard for
configuration. However, you can configure firewall communication, or modify the
existing configuration using the firewall configuration wizard at any later
time. See the following procedures for more details:
The system supports both one-way firewalls - where only outbound ports
are opened - and two-way firewalls - where a selected set of bi-directional
ports are configured. Software and hardware firewall configurations, including
Microsoft Windows operating system firewall and TCP/IP filtering are supported.
The Firewall Configuration wizard creates three files called the
FwPeers.txt, FwHosts.txt
and FwPorts.txt and configures the firewall services
in the on-demand mode, where the tunnels to control traffic are opened
on-demand or when needed. This type of configuration is suitable for two-way
firewalls where connections to ports required by the software can be opened from
both sides. Sample contents of these three files in a two-way firewall are given
below:
The following table lists the entries in the FwHosts.txt
and FwPeers.txt using sample scenarios:
| Description |
CommServe |
MediaAgent |
Agents |
| CommServe and MediaAgent on the friendly
side; Agents on the hostile side. |
Agents |
Agents |
CommServe and MediaAgent |
| CommServe on the friendly side; Agents and
MediaAgent on the hostile side |
MediaAgent and Agents |
CommServe |
CommServe |
All CommCell computers (CommServe, MediaAgents and clients) require the following
port specifications to communicate across firewall(s).
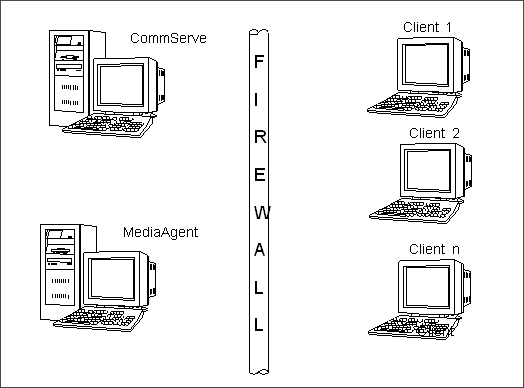
When the CommServe and the MediaAgent(s) are on the opposite side of the
firewall from Client(s)as depicted in the diagram on the right:
| Component |
Port Requirements |
| CommServe |
8400 + 8401 + 1 |
| MediaAgent |
GxCVD Port + Total
number of concurrent restore streams to the MediaAgent + 1
If the data is not multiplexed, this would also be equal to the
total number of drives attached to the libraries in the MediaAgent
+ 1
|
| Client |
GxCVD Port + 1
(If the
Optimize for Concurrent LAN backups option is selected in the
MediaAgent, which is the default setting)
GxCVD Port + Maximum number of concurrent
backup streams from the client + 1
(If the
Optimize for Concurrent LAN backups option is not selected in
the MediaAgent)
|
| NDMP Remote Server |
Port 10000 if you have a NAS
iDataAgent, NDMP Remote
Server and/or NAS filer communicating across firewall(s). |
|

|
If you plan to run other concurrent
jobs (such as Auxiliary Copy or data recovery operations), you must
open additional ports, based on the number of streams used by these
jobs. |
|
 |
| |
|
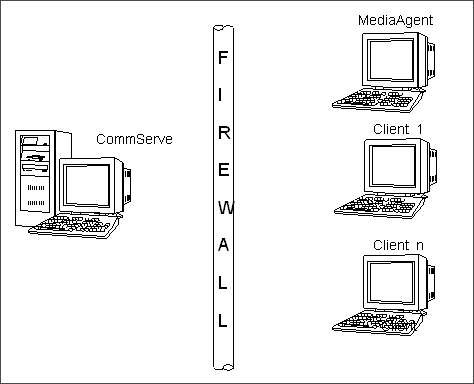
When the MediaAgent(s) and Client(s) are on the same side of the firewall
with the CommServe on the opposite side, as depicted in the diagram on the
right:
| Component |
Port Requirements |
| CommServe |
8400 + 8401+ 1 |
| MediaAgent |
GxCVD Port + 1
|
| Client |
GxCVD Port + 1
|
|
For ContinuousDataReplicator on Unix environments,
the client will require an additional port to be open on both directions
— from source to destination and back. So
the port requirements for the client are GxCVD Port
+ 2 additional ports. |
|
 |
The system also supports persistent one-way tunnels between the CommCell components.
This configuration is useful when the firewall allows programs to open connections
only one-way, e.g., only from CommServe to the Client, but not the other
way around. In one-way firewall, network communications are initiated from the secure/friendly
side of the firewall. The firewall host allows both cases, 1-Way Host Reachable
and 1- Way Host Not Reachable. In such a scenario, the software will open the necessary tunnel
connections as soon as the services are started on the secure side. This way, the
clients on the hostile side of the firewall will be able to accept the tunnel connection
and use it to forward control and data traffic both ways.
As explained in the previous sections, the Firewall Configuration wizard creates
the three files FwPeers.txt,
FwHosts.txt, and FwPorts.txt.
Sample contents of these three files in a one-way firewall are given below:
- The FwPorts.txt lists open incoming ports,
i.e., ports that remote computers can open connections to when they need to
talk to the computer with the FwPorts.txt file.
For example, if you have opened up 20 ports from 8600 to 8619, 10 ports from
8650 to 8659 and specific port like 8800, the following entries will be added
to this file:
8600-8619
8650-8659
8800
- The FwHosts.txt lists all the computers
on the other side of the firewall that the specific computer (in which the Firewall
Configuration wizard is run) will communicate. For example, if the computer
is a CommCell Client computer and if the CommServe and MediaAgent are across
the firewall, this file should contain the names (or the network IP address)
associated with the CommServe and MediaAgent computers. This ensures that only
the connections to the computers listed in this file will be forwarded through
tunnels. Computers on the same side of firewall will be contacted directly.
A sample FwHosts.txt is shown below:
aquila.company.com
perseus.company.com
- The FwPeers.txt is used to configure dedicated
port-forwarders. A sample FwPeers.txt is shown
below:
computer1.company.com @@PASSIVE@@
computer2.company.com computer2.company.com
189.27.271.11 189.27.271.11
Note the following on the contents of this file:
- The computer in the secure side of the firewall (computer1.company.com
in the above example) cannot be reached, and designated Passive.
- The computer in the hostile side of the firewall (computer2.company.com
in the above example) is listed twice.
|
Note that wildcards are not allowed in one-way firewall
configurations. |
Note that in a one-way firewall these ports must be configured as out-bound ports
as follows:
|
When the CommServe and the MediaAgent(s) are on the opposite side of the
firewall from Client(s), as depicted in the diagram on the right, with the
CommServe and the MediaAgent(s) in the secure/friendly side and the clients
in the hostile side, the following ports must be opened:
Conversely, when the CommServe and the MediaAgent(s) are in the hostile
side and the clients in the secure/friendly side, the following ports must
be opened:
| Component |
Location |
Port Requirements |
| CommServe |
Hostile side |
8400 + 1 |
| MediaAgent |
Hostile side |
GxCVD Port + number
of restore streams + 1 |
| Client |
Secure/friendly side |
None |
|
 |
| |
When the MediaAgent(s) and Client(s) are on the same side of the firewall
with the CommServe on the opposite side, as depicted in the diagram on the
right, with the CommServe in the secure/friendly side and the clients and
the MediaAgent(s) in the hostile side, the following ports must be opened:
| Component |
Location |
Port Requirements |
| CommServe |
Secure/friendly side |
None |
| MediaAgent |
Hostile side |
GxCVD Port + 1 |
| Client |
Hostile side |
GxCVD Port + 1 |
Conversely, when the CommServe is in the hostile side with the clients
and MediaAgent(s) in the secure/friendly side, the following ports must
be opened:
| Component |
Location |
Port Requirements |
| CommServe |
Hostile side |
GxCVD Port + 1 |
| MediaAgent |
Secure/friendly side |
None |
| Client |
Secure/friendly side |
None |
|
 |
Firewall services for remote clients can be configured using registry keys.
You can use Active Directory Group policy Objects (GPOs) to push out the registry keys
to multiple
remote client computers simultaneously. This is particularly useful when you have to update
firewall configuration for multiple remote clients, like Workstation Backup Agents.
The following registry keys provide firewall configuration:
- The FWHost
registry key contains values for the FWHosts.txt
file. Create one key for each host. For example, if you have three hosts,
then create keys FWHost1, FWHost2, and FWHost3 with appropriate values.
- The FWPorts
registry key contains values for the FWPorts.txt
file. Create one key for each port range. For example, if you have two port
specifications, then create FWPorts1 and FWPorts2.
Once you create the above keys on the client computer and recycle
Services, the three firewall files
FWHosts.txt, FWPorts.txt, and FWPeers.txt will
be created, overwriting any existing firewall configuration.
Port 8401 must be opened on the CommServe (both in one-way or two-way firewall
configurations) when the CommCell Console is installed or accessed as follows:
- When the CommCell Console is installed on the CommServe computer and will
be accessed remotely from other computers across the firewall
- When the CommCell Console is installed as a stand-alone application, (without
any other component on that computer, e.g., on a different IIS computer) and
if the computer on which it is installed is across firewall(s) from the CommServe.
If you intend to use the CommCell Console remotely through a web browser, then
in addition to allowing connection for port 8401 through the firewall, ensure that
the http service port, which is typically port 80, is also allowed connection in
the firewall.
Note that other than opening the necessary ports, it is NOT necessary to use
the Firewall Configuration Wizard to configure the firewall configuration files
for a stand-alone CommCell Console.
- Verify the following, if operations across firewall(s) are not working:
- You have opened all the necessary ports in the respective firewall.
- The range of ports is specified in the firewall configuration wizard. Use the
CommCell Readiness
Report to verify whether the ports are correctly configured.
- You have included the correct ports in the appropriate computers.
- You have the appropriate Host Names or IP Addresses of all the computers
that are separated from a computer by firewall(s).
If your network administrator
allows you to disable/remove the firewall(s), then try running the backup/restore
that way. This will eliminate other causes of failure and pinpoint the problem
on firewall subsystem.
Contact your software provider for assistance if all the above mentioned
verification is successful and you continue to experience failures during
data protection or data recovery operations.
- Windows XP (SP2) and Windows 2003 (SP1) both include an optional firewall
that can be enabled. As a result all the data protection jobs from that computer
may go into the Pending state. Hence you must
open the appropriate ports as described in Port
Requirements from the Windows firewall. Alternatively, you can also disable
the Windows firewall if you have another firewall enabled for the computer.
The following section describes the firewall settings in
NOKIA CHECKPOINT 4.1 (with SP5).
- Open the init.def file located in the
<firewall install directory>/lib directory.
- Stop the firewall services using the fwstop
command.
- Using a text editor, edit the init.def file.
- Add the following command before the line ADD_TCP_TIMEOUT(0,0)
for each of the firewall ports that are open:
ADD_TCP_TIMEOUT(port,timeout)
Where
port is the TCP service port
timeout is the desired timeout in seconds.
For example if you want to open the ports 9500 through 9503 with a timeout
value of 30 minutes, you must have the following entries:
ADD_TCP_TIMEOUT(9500,1800),
ADD_TCP_TIMEOUT(9501,1800),
ADD_TCP_TIMEOUT(9502,1800),
ADD_TCP_TIMEOUT(9503,1800),
- Restart the firewall services using the fwstart
command.
See Firewall Considerations - NAT Server
for information on connecting CommCell to a NAT server across the firewall.
The following section provides information on firewall configuration:
Bull Calypso Communications Service (GxCVD) uses port 8400 by default. If you
are using a non-default port, you need to open up the
corresponding port in the firewall. You can specify a non-default port
number for GxCVD in following ways:
|
The ports used by Bull Calypso
services must not be used for other configurations.
Verify the service port assignments before using a port for firewall configuration. |
All CommCell Computers interacting with one another across a firewall need not
necessarily use the same ports. Consider the following:
- Reserved ports must be between 5000 and 32767.
- For added security, it is recommended that you configure the firewall to
accept only connections to and from CommCell computers on the opposite side
of the firewall.
- Use the
CommCell Readiness
Report to verify whether the ports are correctly configured.
- The total number of ports in use will vary depending on the operations occurring
at any given time.
- Due to the port-forwarding overhead, data restore operations will run slower
compared to the two-way firewall and no firewall configurations. Also, data
backup operations toward MediaAgents with the Optimize for concurrent LAN
backups option enabled (default), will run slower as well. Therefore, it
is recommended to disable the Optimize for concurrent LAN backups for
one-way firewalls.
- In a one-way firewall setup, whenever you install a new client in the CommCell,
run the firewall configuration wizard on the CommServe and add the name or IP
address of the client computer before installing the software on the client.
- Data recovery operations across one-way firewall on NetWare are not supported.
Hence you should open your firewall both ways for performing data recovery operations
on NetWare Clients.
In a firewall configuration, if the client computer has multiple instances of
the Agent software installed, then each instance must be configured with a
distinct IP address and hostname, to be uniquely identified by the CommServe.
-
The firewall configuration files (FwPeers.txt,
FwHosts.txt and
FwPorts.txt) are also included in the Disaster Recovery backup. If
necessary, the entries associated with Clients/MediaAgents on the other side of
the firewall from the CommServe can be restored in the event of a
CommServe re-build. Note that a restore of the disaster recovery backup does not
automatically restore the firewall files. To restore these files, manually
select these files for restore from the
CommServe Disaster Recovery Tool. See
Restore a Disaster Recovery Backup for step-by-step instructions.
-
If necessary the Send Log Files option can be used to send the firewall
configuration files.
-
If a MediaAgent or
Client on a Microsoft Windows MSCS virtual server needs to communicate with
other CommCell components across a firewall, you must:
- Install File System iDataAgent or MediaAgent on all the
physical nodes of the cluster. During the installation, use the firewall related
prompts to establish the firewall settings required by the software to
communicate across the firewall.
- Then install the software components on the virtual nodes. (It is not
necessary to configure the firewall settings again in the virtual nodes.)
If the cluster communicates with the CommServe across a one-way firewall, you
must add both the physical and virtual nodes' host names (or the IP addresses)
in the CommServe computer before installing the software.
- To enable uninterrupted communication from NAS file servers across the firewall,
the CommCell selects a open port based on the firewall configuration and directs
the NAS file servers to connect on that port.
-
If SRM clients are connected to a SRM Server that is firewall protected,
then port number 443 must be open in the SRM Server computer to successfully
view SRM reports from the clients computers.
If you have more than one client in the CommCell resolving to the same IP address, then the following configuration
will ensure unique client identification within the
CommCell:
- The clients must be configured as if they are behind a firewall, with the configuration
1-way firewall -
Host is reachable from this machine (clients can contact the CommServe,
but the CommServe cannot contact the clients). Choosing the 1-way firewall
option (even if there is no firewall in between the client and the
CommServe) forces the client to initiate all communications within the
CommCell. All communications happen over the channels that are
created from the clients towards the CommServe, so there is no scope for
conflict.
Firewall configuration for
the client is defined during the
Installation.
Post installation, you can use the Firewall
Configuration Wizard to set up the firewall configuration. For
step-by-step instructions, see Firewall Considerations - How To.
- The clients resolving to the same IP address or to the same fully
qualified domain must be identified with a unique client name and a unique
host name within the CommCell.
Note that the host names can actually resolve to same IP address as the
CommServe never initiates a communication towards the client in this
configuration.
This information is provided in the Communication Interface Name dialog
during the installation. If the clients are not uniquely identified, then you will have to reinstall the
client with the appropriate firewall settings. See
Installation.
The application firewall can be used to block any rogue sessions from other
CommCell Components. The firewall also provides option to block any undesired connections
from local as well as remote computers.
When a remote client is force deleted from the CommServe, the
services for the client would be still
remain active. Such client would still be able to initiate sessions. Communications from
such unauthorized clients
would affect the performance of the software, especially if they
grow more in number. CommCell Clients can be configured to block such connections. The
session blacklisting works as follows:
CommCell validates every incoming connection, and if it identifies an unauthorized connection, the IP
address of the client initiating the session is added
to a session blacklist. Any subsequent connection from a blacklisted client is
immediately denied without verification. This list is dynamically created in
each client. Optionally you can also record the list of blacklisted clients in a
log file. When enabled, the log file is created in the following location - <Software_Installation_Path>/Log Files/Blacklist.log.This
file can be used to review the list of client that are blacklisted.
To enable (or disable) session blacklisting, see
Block
Unauthorized CommCell Session Connections for step-by-step instructions.
Application firewall allows you to protect your computer from undesired
remote connections. The list of external IP addresses you wish to block
connections from can be stored in a blacklist (InterfaceBlacklist.txt), a list of external interface
connections to be blocked. This file is created in the <Software_Installation_Path>/Base
folder for each client, and can be modified at any time. The feature is not
enabled, if this file is not present.
To block connections from a remote computer, simply add the IP address of the
computer to the blacklist. When a new connection is initiated, the software consults the blacklist,
and if a connection is found to be initiated from a blacklisted external address, the
connection is dropped.
For step-by-step instructions to create the external interface blacklist, see
Block External Interface Connections.
You can also use the application firewall to protect your computer from undesired connections to local interfaces. The list of local IP addresses (or host names) that the application has to block connections on, is stored in
LocalInterfaceBlacklist.txt. This file is created in the
<Software_Installation_Path>/Base folder for
each client, and can be modified at any time. If modified, the services must be recycled
for the changes to take effect. The feature is not enabled if this file is not present,
or empty.
When there is a new incoming connection, the local interface to which the connection arrived is checked against this list,
and if found, the connection is immediately dropped without any further processing.
For step-by-step instructions to create the local interface blacklist, see
Block Local Interface Connections.
Windows Firewall, the built-in firewall included in the Windows Operating Systems, can be configured to allow CommCell communications by adding CommCell programs and services to the Windows Firewall Exception list. Once the CommCell programs are added to the Exception list,
the Windows Firewall will allow the external network connections made to the programs in this list. The exceptions must be added to
Windows Firewall on all the CommCell Computers.
CommCell programs and services can be programmatically added to the Windows Firewall
Exception List using the AddFWExclusions.bat.
For step-by-step instructions, see
Add Exceptions to Windows Firewall.
Note that if for any reason the firewall configuration is reset on a computer (this
can happen, for example, when the computer is moved from a workgroup to a domain), then the firewall exclusions must be added again.
Back To Top


